Strategies to Prevent System Misuse and Resource Overload
(4 Minutes) | How to Protect Your System from Misuse and Resource Drain
Get our Architecture Patterns Playbook for FREE on newsletter signup:
Build Scalable Applications With Ease
Presented by Render
Wish you could build full-stack apps without the infrastructure headaches? From startup to scale, Render handles the heavy lifting — built-in vertical scaling, fault tolerance, and network security, so you can move fast without sweating reliability or performance bottlenecks.
Spend more time building and less time maintaining with the cloud application platform developers love.
Strategies to Prevent System Misuse and Resource Overload
Mass adoption is any system or application’s dream.
But with that comes the risk of misuse and resource overload.
Measures should be in place to ensure the quality of service across all users.
Last year, there was a well-known case of Twitter/X facing this exact problem.
Their solution? Rate limiting. This involved restricting the number of requests a user or service can make on a system.
While it's certainly a viable solution for many cases, it isn't the only one. Let's look at some other alternatives that can be implemented into any system.
It's important to note that these solutions should be implemented defensively to avoid scenarios requiring ad hoc remedies.
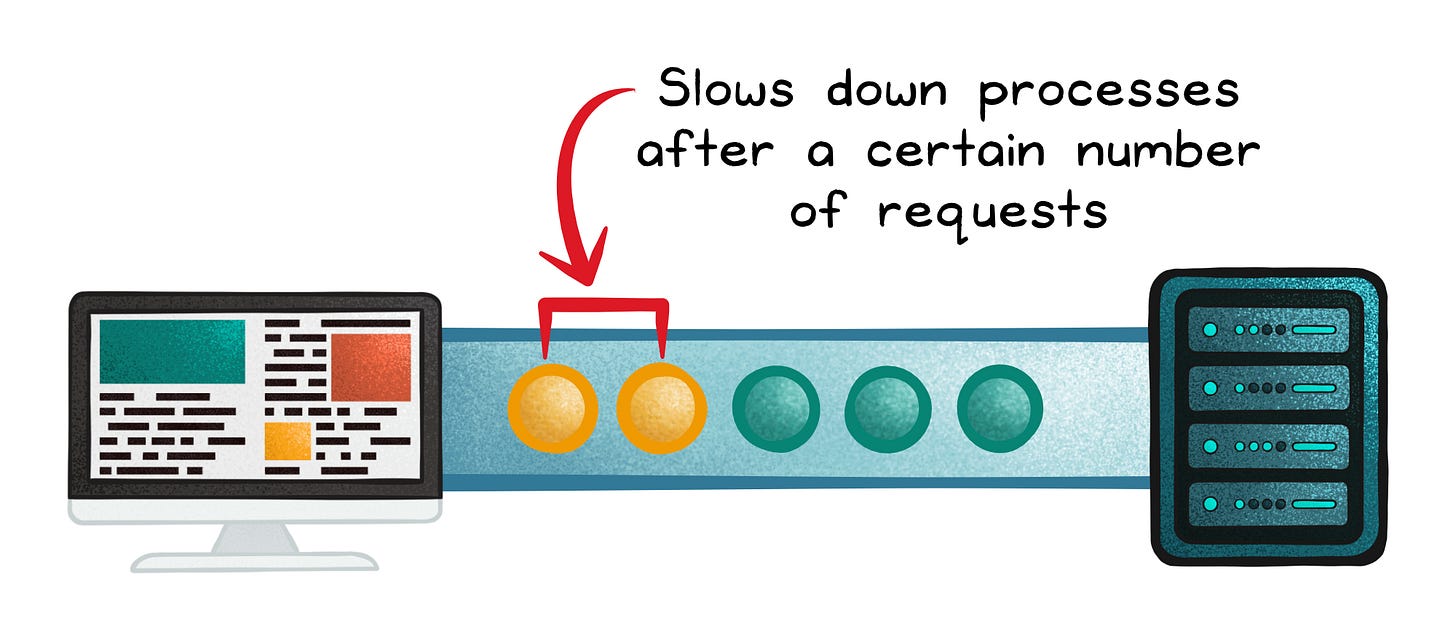
Throttling
Throttling is a simple technique that slows the time it takes to process a task in order to minimize resource consumption.
This is often used in conjunction with quotas or rate-limiting so that users aren't entirely cut off from the service but instead, the quality of service is lowered to a reasonable level.
This is a popular approach internet service providers take to minimize bandwidth congestion during peak traffic. Similarly, throttling requests on a server or API is also commonly done in software systems.
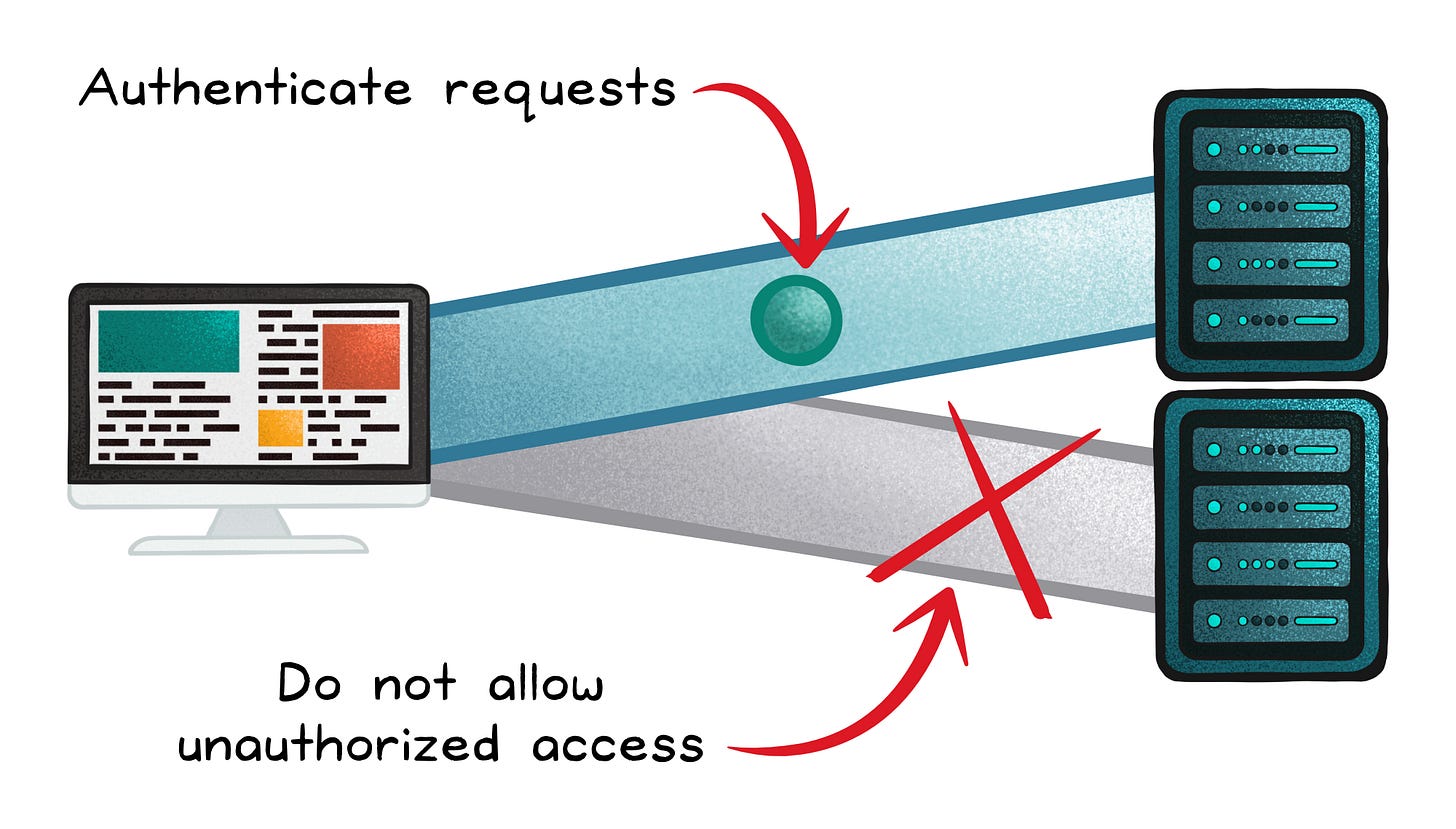
Authentication and Authorization
These are important security measures that minimize the risk of service misuse and denial of service attacks (DoS).
It also helps identify and limit the access of bots and scraper accounts.
First, the requesting user or service would be verified and identified using a username and password or more sophisticated methods such as 2FA. Once they have been identified, the system would then determine which resources the requester can have access to and their level of priority to the system’s resources (if applicable).
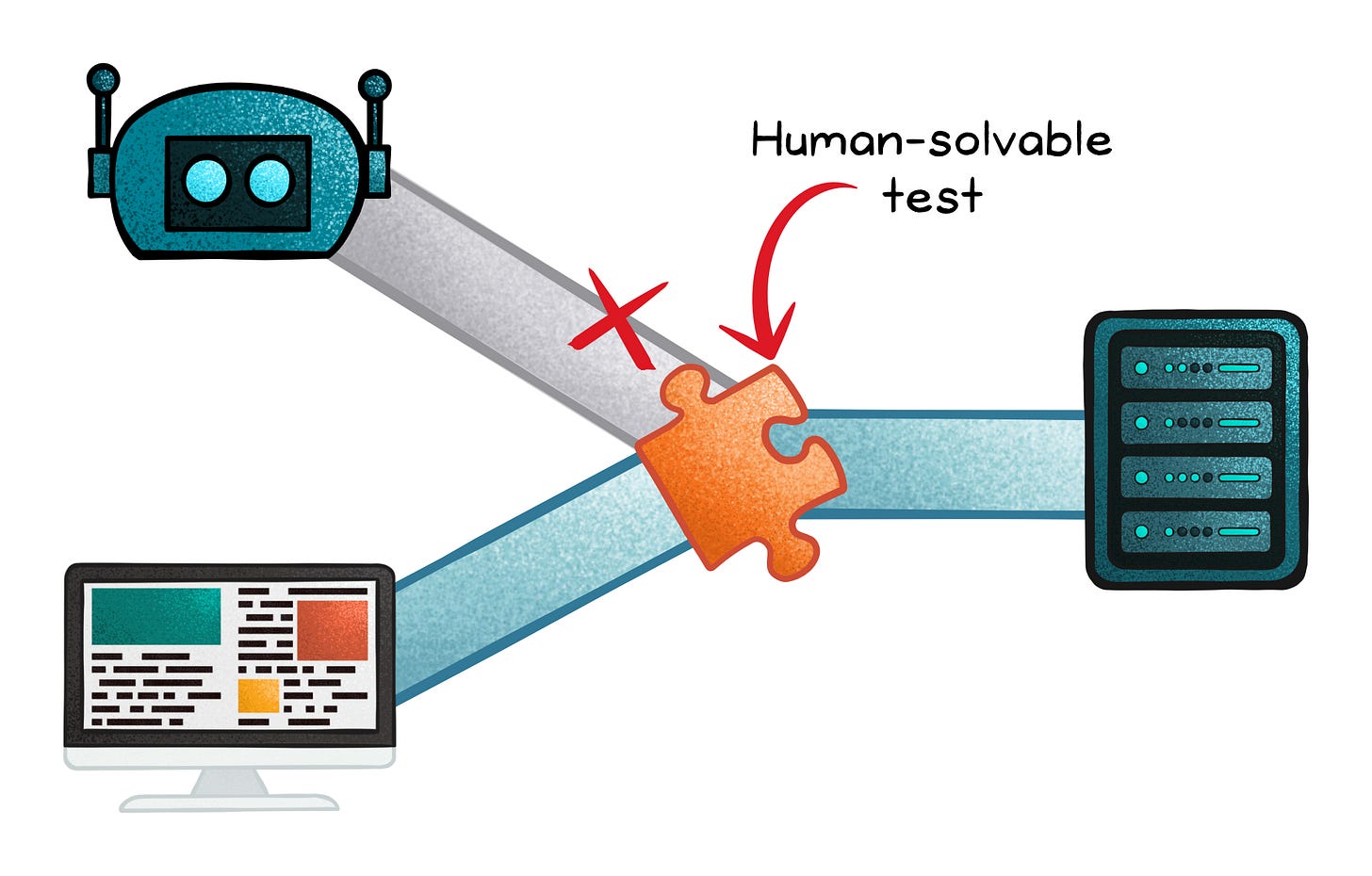
CAPTCHA
CAPTCHA aims to identify human requesters and deny access to bots. It does so by introducing human-solvable tests before granting access to the service or certain features.
While this technique is a popular approach, its impact on the application’s accessibility is a notable consideration.
You would have noticed CAPTCHA tests have become increasingly challenging in recent years. AI technology is making it increasingly difficult to distinguish between human requesters and bots so the challenges are becoming more difficult.
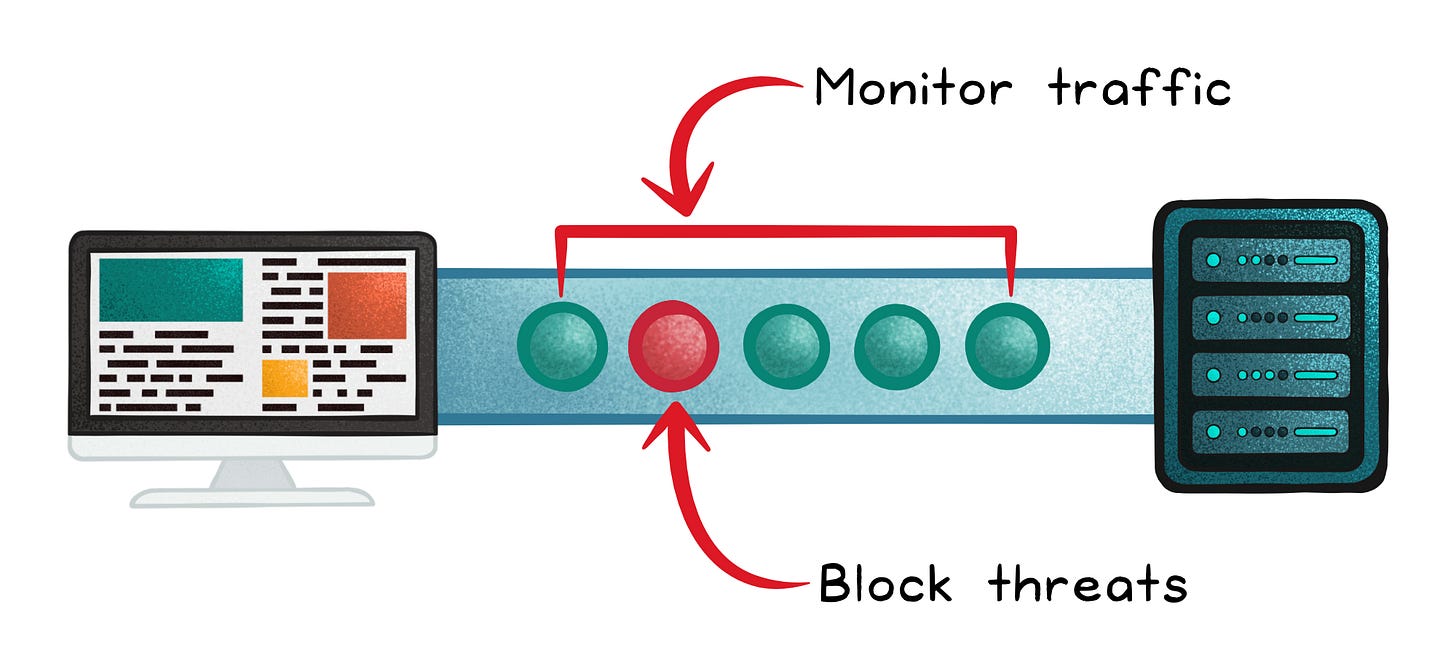
Intrusion Detection and Prevention Systems
Specifically used to mitigate the risk of system attacks, this approach involves monitoring network traffic to identify malicious activity.
Intrusion Detection Systems (IDS) are used to alert and report on identified threats, whereas Intrusion Prevention Systems (IPS) aim to block them.
Beyond the requirement of identifying and blocking threats, some other solutions that prevent system overload are:
Load balancing: distribute requests across multiple servers.
Prioritization: ensuring critical requests have priority to system resources.
Circuit breaker pattern: prevent task retries that are likely to fail.
Concurrency limits: limit the number of connections that can be made to the system or the number of concurrently running tasks.
Preventing system overload and misuse requires a full team effort to employ defensive engineering. The techniques mentioned above should be implemented carefully to ensure legitimate requests are not restricted.
A combination of multiple strategies should be used to develop a full-system approach that suits your system’s unique use case.
Subscribe to get simple-to-understand, visual, and engaging system design articles straight to your inbox: